Wednesday 28th March, 2018
Show and Tell 42
James and I were joined by Tom, Ben, Chris and first-time show-and-teller Tom for our 42nd Show & Tell evening.
Yubikey
Chris has recently taken on a role at work that involves greater access to production systems. His team’s use of Yubikey’s as part of their approach to security prompted Chris to simplify and harden the security around all his passwords and sensitive data.
The Yubikey offers 2-factor authentication by being “something you have” alongside “something you know” (Chris memorises a password). There are various types of Yubikey available. Chris showed us the USB-C version which works with recent Macbooks. There’s also an NFC version which would work with some laptops and smartphones.
Chris then went on to explain how the Yubikey fits into the system he now uses to secure all of his accounts and sensitive documents.
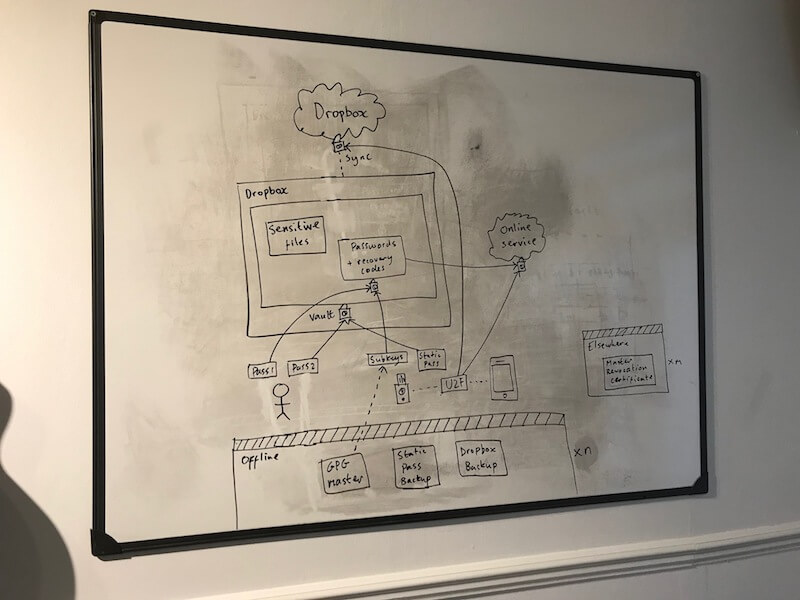
Chris uses an encryption software called Cryptomator that creates an encrypted folder in his Dropbox. The master password for this vault is a password he remembers concatenated with one generated by pressing the button on the Yubikey. Inside the vault is a file that contains passwords and recovery codes for other services as well as other sensitive files.
Where possible Chris also likes to use the Yubikey’s Universal 2nd Factor support to log in to online services. Google, Github, Dropbox and others support this standard.
Sliding Puzzles
Chris then gave us a preview of a topic he’s going to talk about in more detail at the April London Ruby User Group meeting: sliding puzzles.

Chris was inspired to play around with sliding puzzles after seeing one mentioned in one of Alan Turing’s papers during a visit to Bletchley Park. It turns out that Sliding Puzzles are used as a model problem in computer science due to their combinatorial complexity. For example, a 4x4 puzzle with one missing tile (a “Fifteen puzzle”) contains 16!/2 (around 10^13) states. Storing all of these states in memory would require a huge amount and therefore calculating the shortest path to a solution, for example, is a tough problem.
Chris talked us through some strategies for solving the puzzles efficiently including using invarients (ruling out some moves immediately due to their configuration), and pre-computing solutions to store in an “oracle”. Chris has also been learning Rust by applying it to this problem and has some code to pre-compute puzzles much faster than can be done in Ruby.
If you want to learn more - be sure to attend Chris’s LRUG talk.
Ethereum
Tom C showed us something he’s been working on with the Ethereum platform. Starting with the observation that the maximum number of transactions that crypto-currencies like Bitcoin can handle is quite a lot less than what a modern credit-card system like Visa can handle, folks have been thinking of ways to speed things up.

One approach is to perform transactions on a “side chain” and then periodically reconcile them with the main blockchain. Using such strategies opens up new avenues for bad actors to exploit, and Tom has been researching how these attacks might work and how best to prevent them. The theory uses mathematics derived from the study of games and how, for example, to decide who wins a game if one of the players decides to not complete their move.
Parsec
Ben rounded off the evening for us by giving a quick demo and explanation of Parsec. Ben’s son really wanted to play a game that’s only available on Windows. There’s no Windows machines in Ben’s house so Ben first tried to create a virtual machine on Amazon’s AWS service to run the game. This worked OK, but suffered from some latency that made the game difficult to play. After some research they discovered Parsec which allows virtual gaming machines in the cloud to be efficiently streamed to a local machine. Ben’s really impressed with how easy it was to set up and the performance. And his son got his gaming fix!

If you have any feedback on this article, please get in touch!
Historical comments can be found here.