Friday 31st August, 2018
Serving our website securely
We recently decided it was high time we started serving our company website over SSL.
I logged into our Linode VPS and attempted to follow these instructions for using the certbot tool on Ubuntu Trusty with Apache. Generating the certificate for our bare domain, gofreerange.com, from Let’s Encrypt worked fine, but I ran into problems with the automatic changes to the Apache config. See this commit note for more details.
The main outstanding issue was that https://www.gofreerange.com (i.e. the www sub-domain over SSL) resulted in an error in Firefox and Safari, although apparently not in Chrome.
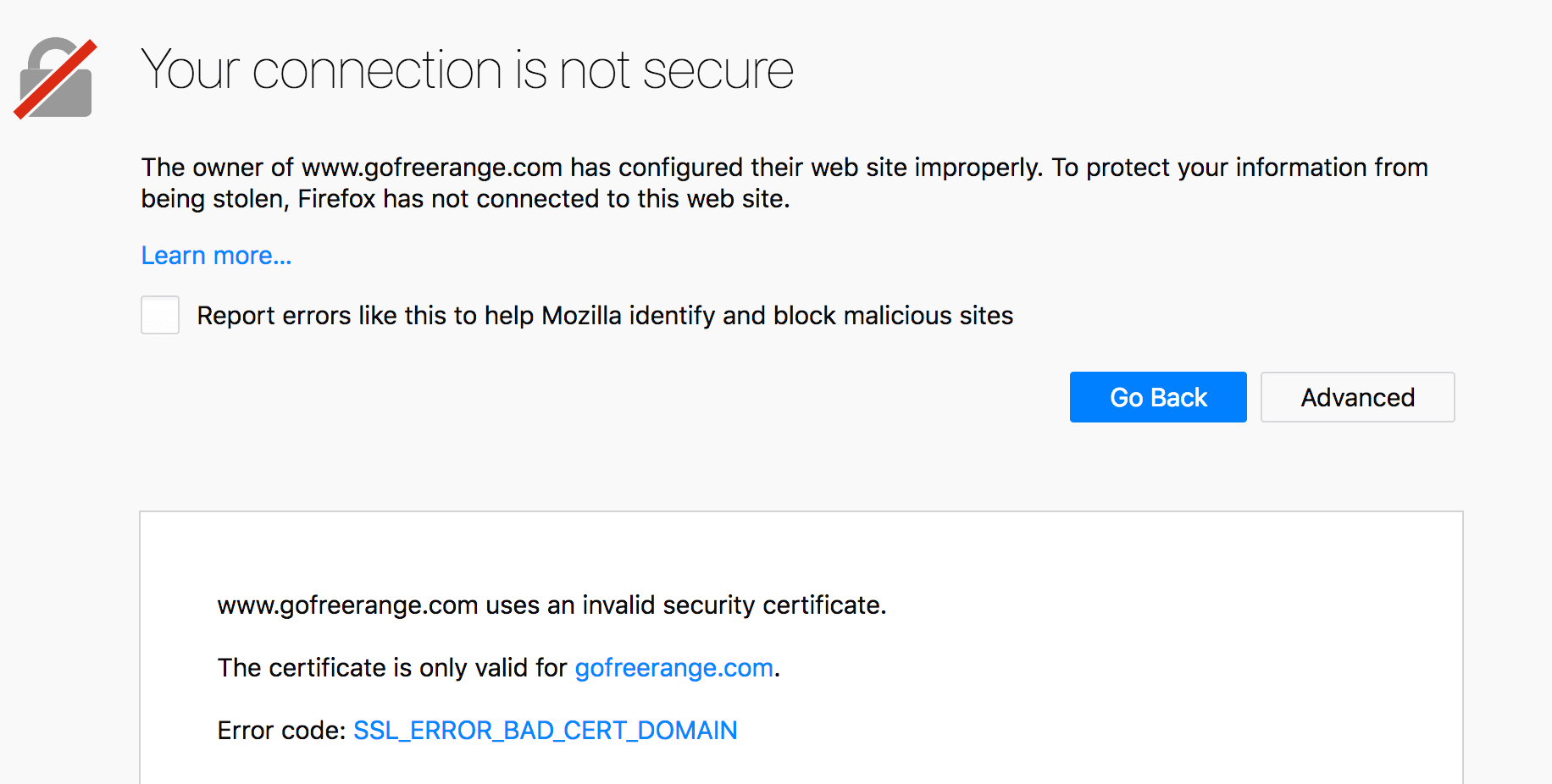
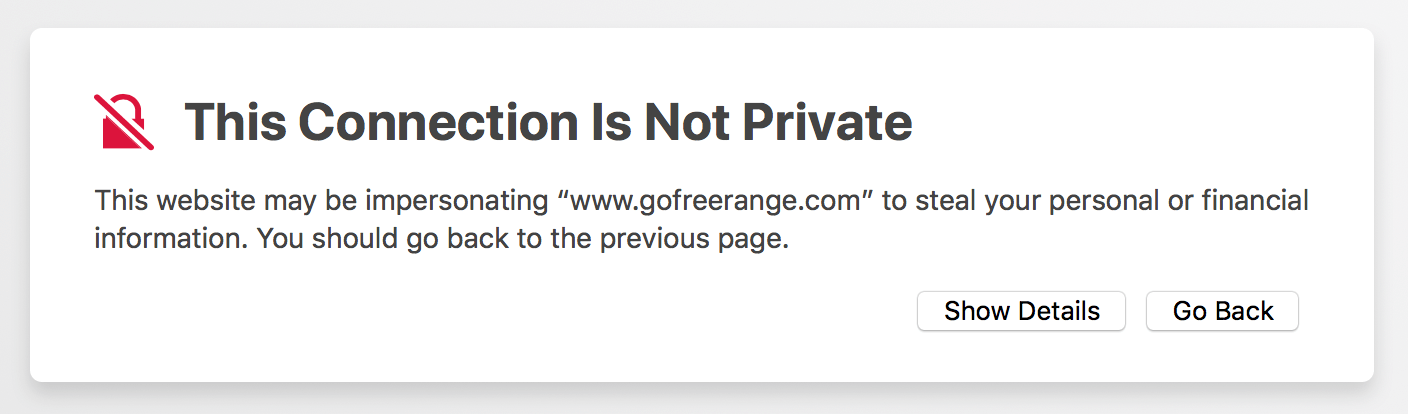
I belatedly realised that to fix this problem I’d need to generate and install a certificate for the www sub-domain. So having generated this new certificate, I setup an Apache virtual host for www.gofreerange.com listening on port 443, configured the certificate, and adjusted the redirect rules to give the following behaviour. See this commit note for further details.
http://www.gofreerange.com->https://www.gofreerange.comhttp://gofreerange.com->https://gofreerange.comhttps://www.gofreerange.com->https://gofreerange.comhttps://gofreerange.com(no redirect; served successfully)
I also belated realised that switching over to serving the site over SSL meant that I needed to fix a bunch of URLs to avoid mixed content warnings. I concentrated on fixing the mixed active content and I think this is all done, except for the video sources & poster image in these week notes.
Having said that neither Chrome nor Safari complain about the latter being mixed content - only Firefox does. Fixing the problem would mean either setting up an SSL certificate for the videos.gofreerange.com S3 bucket or using an alternative video provider, e.g. Vimeo. I decided that could wait for another day.
Both SSL certificates are managed by the certbot tool and so it should be easy to renew them. I followed the instructions from the output of the certbot tool to backup the /etc/letsencrypt directory which contain certificates and private keys.
I also noticed that certbot seems to have installed a cron job into /etc/cron.d/certbot which attempts to renew all certificates twice a day which is pretty nifty. I added a one-off Harmonia task to check that the certificate for gofreerange.com is renewed successfully just before the 90-day expiry.
Finally everything seemed to be working OK, so I updated our monitoring systems to point at the SSL-version of the URLs. And here it is in all its glory!
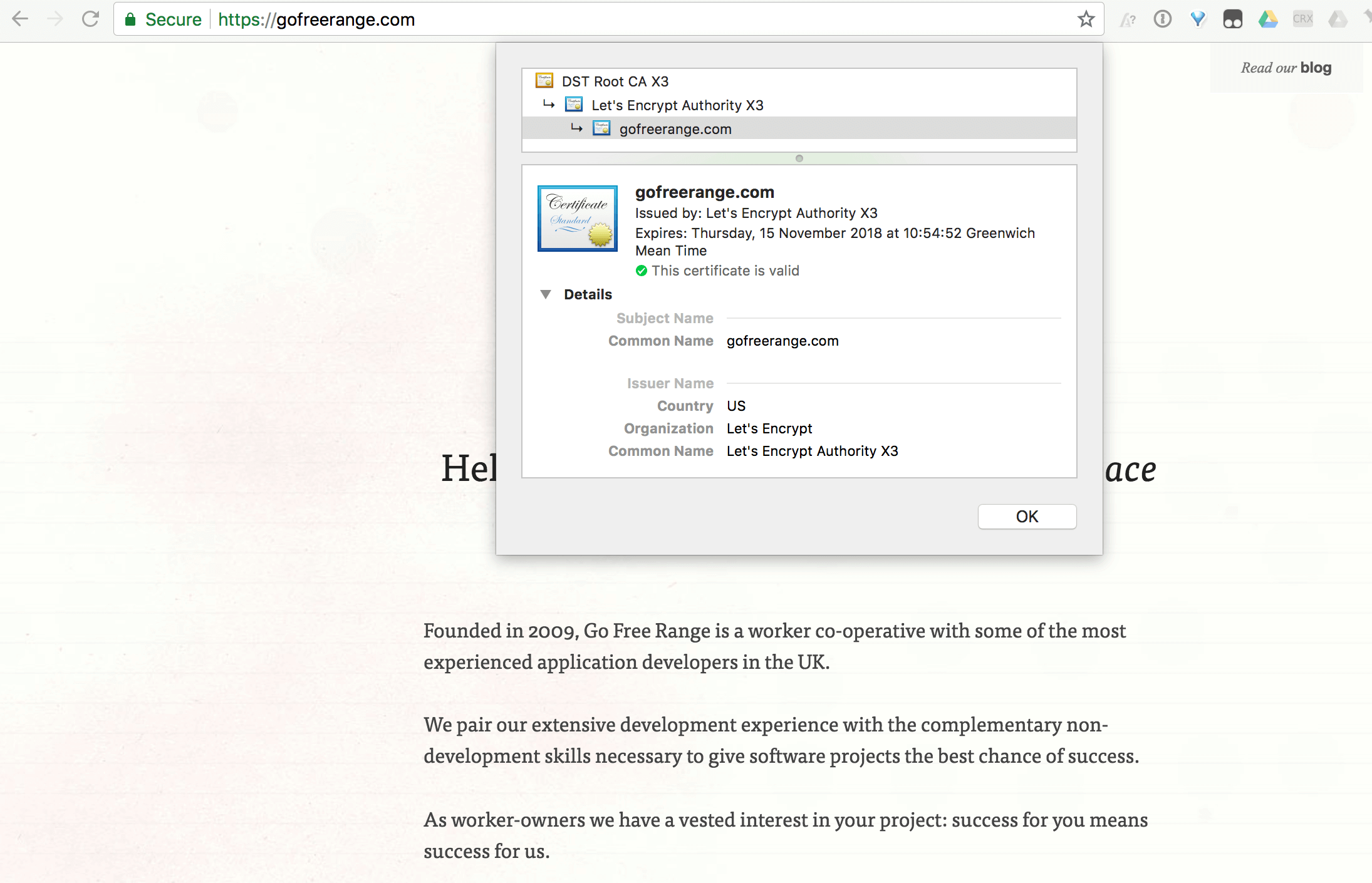
I hope that was useful!
– James

If you have any feedback on this article, please get in touch!
Historical comments can be found here.